Google was forced to cancel an Android event planned for this morning
due to Hurricane Sandy, but the company still went ahead and revealed
its revamped Nexus lineup
in a blog post.
As rumored, a new Nexus phone manufactured by LG will take over as
Google’s flagship handset, while an updated Nexus 7 tablet alongside an
all-new Nexus 10 model will place a bit of pressure on Apple’s iPad
lineup.
Nexus 4
The
Nexus 4 smartphone
features a 1.5GHz quad-core Snapdragon S4 Pro processor, which Google
touts as the fastest on the market, as well as a 4.7-inch 1280 x 768 IPS
display, 2GB of RAM, dual cameras (1.3MP front, 8.0MP back), and either
8GB or 16GB of internal storage. Google also baked in NFC support and a
wireless charging feature that lets you power the phone by setting it
down on an inductive “
Charging Orb”.

The latter is somewhat reminiscent of the Palm Touchstore, with the
face of the dock set at an angle so you can easily see the phone when
charging and magnets inside the Orb preventing it from sliding off.
Google says the Nexus 4 uses the Qi wireless charging standard, so
charging pads designed for Nokia's Lumia phones should be compatible
too.
On the software side, the Nexus 4 introduces
Android 4.2 as a new flavor of Jelly Bean, with support for Miracast (an
open alternative to Apple’s Airplay),
a new gesture typing keyboard similar to Swipe, a feature called Photo
Sphere for creating 360-degree panoramas, among other improvements.
One feature notable missing is support for LTE networks, though. According to
The Verge,
Google left this feature out in order to have complete control of the
software with no carrier intervention -- apparently there's no access to
LTE networks without working with carriers in one way or another.
As a result, the Nexus 4 will only be available as an unlocked HSPA+
device starting on November 13 in the US, UK, Canada, Germany, France,
Spain and Australia, with other markets around the world getting the
phone towards the end of the month. The device will sell for $299 with
8GB of storage or $349 with 16GB. A T-Mobile version will sell unlocked
for $199 on a two-year contract.
Nexus 7
Next up, Google announced a couple of updates for the
Nexus 7 tablet
introduced this past summer. The first relates to storage capacity,
which now starts at 16GB for the same $199 or 32GB for $249, and the
second is a new model with 32GB of storage and HSPA+ mobile data
compatible in 200 markets for $299.
Otherwise, the design of the Asus-made tablet as well as the rest of
the specs remain the same. The new Nexus 7 (32GB + Mobile) will be sold
via the Google Play Store starting November 13.
Nexus 10
Lastly, Google announced Samsung as its hardware partner for a larger
Nexus 10 tablet
to rival the full-size iPad. The device features a dual-core ARM
Cortex-A15 chip paired with 2GB of RAM, as well as a 10-inch screen at
2560 x 1600 resolution, clocking in at 300ppi. There’s also a 5MP camera
on the back, a 1.9MP camera on the front, and a 9,000mAh battery that
Google says runs for 9 hours.
Other features include microUSB, Micro HDMI and not one but two NFC chips.
The Nexus 10 also ships with a stock version of Android 4.2 featuring
some tablet-specific improvements. Among them is multiple user support
for easier sharing (each user gets their own apps and data), a
"Daydream" mode that's essentially a screensaver, and a number of
accessibility improvements.
The tablet will be available in 16GB and 32GB variants for $399 and
$499, respectively, or essentially $100 less than a comparable iPad with
Retina display. That price coupled with the device’s high-end specs
make this -- at least on paper -- the Android tablet to have in the
upper end of the spectrum. But while Android has been incredibly
successful in the smartphone arena it still needs to up its game when it
comes to tablets, specifically with apps designed with tablets in mind
rather than stretched out versions of their smartphone counterparts.
It will be available November 13th in the US, UK, Australia, France, Germany, Spain and Canada.
Other announcements
In addition to the new hardware, Google also announced updates to its
voice assistant feature Google Now, which now offers flight information,
restaurant reservations, hotel confirmations and shipping details.
Meanwhile, Google Play is getting new video content and is launching the
music store in Europe.

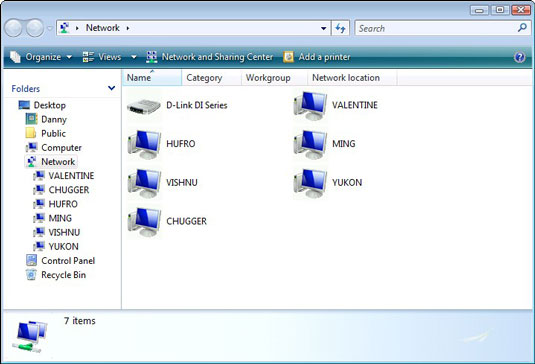 In Windows Vista, open a computer icon in the Network window, shown
above, to see whether any folders or disk drives are available.
In Windows Vista, open a computer icon in the Network window, shown
above, to see whether any folders or disk drives are available.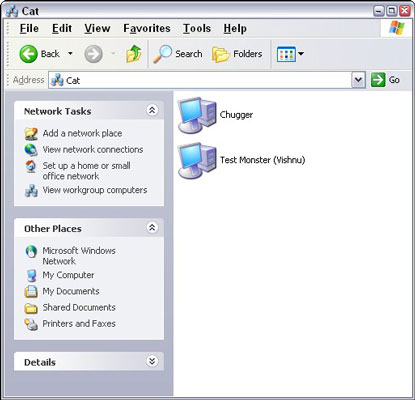 In Windows XP, shared
In Windows XP, shared 













