The following steps use the Final Cut Pro HD generator called Text,
which is the quickest, easiest way to get basic, static text up on the
screen. However, these steps work the same way if you want to apply
other text generators. If you mess up any of these steps, don't worry
about it! You can always undo an action by pressing Command+Z.
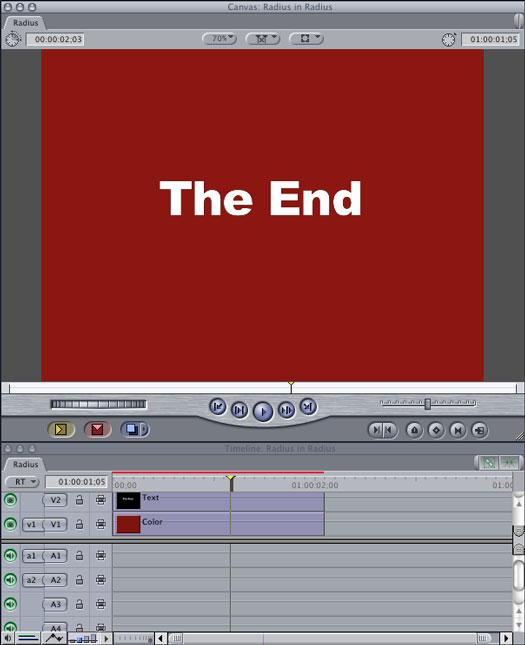
Figure 1: When placed on top of another clip on the Timeline, the text generator clip is superimposed on the clip beneath it on the Timeline (in this example, a plain-colored background).
1. Open the Viewer window by choosing Window --> Viewer from the main menu.
You can also press Command+1 to open the Viewer.
2. Click the Effects tab in the Browser window.
3. Twirl down the small triangle next to the Video
Generators bin, and open the Text sub-bin, which contains the text
generators.
4. Double-click the generator named Text (which looks like a small clip with some color bars on it) to open it in the Viewer.
After you open the Text text generator in the
Viewer, you can see white text that reads SAMPLE TEXT on the Viewer's
Video tab; the Viewer window also sports a new tab titled Controls.
5. Drag the Viewer Controls tab outside the Viewer so that it opens in its own window.
This new Controls tab window lets you type text
and edit it, but the Video tab in the Viewer is where you see what the
text actually looks like while you finesse it. By dragging the Controls
tab outside the Viewer (so that it's in its own window), you can tweak
the text and see it displayed in the Viewer's Video tab at the same
time.
6. On the Controls tab (now in its own window), replace SAMPLE TEXT and make changes to your text.
To do so, highlight SAMPLE TEXT in the Text
field on the Controls tab window and replace it with your own text. For
example, you may want to type The End.
7. Tweak the other settings on the Controls tab, if you want.
The other settings in the Text generator
Controls tab work like a basic word processor. For example, you can
change the font by using the Font pop-up menu. You can also change the
location where your text appears on-screen by clicking the Origins cross
hair in the Controls tab. Your mouse pointer becomes a cross-hair
symbol, and you can then click anywhere in the Viewer window to
reposition your text at that spot.
Unfortunately, the Achilles
heel of the standard Final Cut Pro Text text generator is that it
doesn't let you apply different settings to different parts of the text.
All the text has to be the same font, size, and style.
When you make changes, you should see them
reflected in the Viewer Video tab. If not, click the Viewer window once,
and this should wake it up so that it shows changes while you make
them. Then go back to the Controls tab window and tweak away!
8. Change the duration of the generator's text.
By default, all generators create a clip of
text that lasts for 10 seconds (after you add the generator's text to
your Timeline). To change this setting, highlight the timecode in the
Duration field (located in the upper-left corner of the Viewer Video
tab) and type a new duration, such as 5:00 for a duration of 5 seconds.
Of course, after you place your text on the Timeline, you can also
adjust the text clip's length by dragging the clip's edges, just like
any other media clip.
9. Move the generator's text to the Timeline to
superimpose it over an existing video clip or to make the text appear
over a black background, as follows:
• Superimposed over video: To
superimpose the text clip over a video clip (for example, to display the
name of a person who is currently on camera), first move your video
clip to the Timeline, making sure that the Timeline playhead is over
this clip. Next, drag the generator's text from the Viewer to the Canvas
window, and then select the Superimpose option from the Edit Overlay
that appears over the Canvas. The Superimpose edit places the text in a
new video track, above your video clip. What's more, Final Cut Pro
automatically adjusts the duration of your text to match that of the
underlying video clip. Figure 1 shows a text clip superimposed in the
Timeline over a video clip.

Figure 1: When placed on top of another clip on the Timeline, the text generator clip is superimposed on the clip beneath it on the Timeline (in this example, a plain-colored background).
• Appearing over a black background: If
you want the text to appear over a black background (for instance, if
you're designing an opening title card), you can drag the text from the
Viewer Video tab down to a video track in the Timeline.
10. If necessary, render the text and play it on the Timeline.
If Final Cut Pro is set up for real-time
previews of effects, you don't have to render the text to play it. If
you see a thin, red bar drawn over the text generator clip in the
Timeline, the text clip needs rendering. Select the text generator clip
on the Timeline, and then choose Sequence --> Render --> Both from
the main menu. After Final Cut Pro completes the rendering, place the
playhead just before the text generator clip in the Timeline and press
the spacebar to play through the text.
If Final Cut Pro is set up
to show real-time previews of text without rendering, the Timeline shows
a thin, green bar over the text clip. The text quality you see playing
from the Timeline may seem a bit soft or otherwise rough because Final
Cut Pro is showing you a lower-resolution preview of the text. When you
finally print the movie to tape or export it to a QuickTime digital
file, Final Cut Pro renders the text. To see how clearly the text clip
appears when it's rendered, select it on the Timeline and choose
Sequence --> Render --> Both.
11. Make further adjustments to the text generator by double-clicking it on the Timeline.
Like any clip, the generator opens in the Viewer window, and you can use its now-familiar Controls tab to make tweaks.
After altering any of the text generators, you can drag
the text from the Viewer Video tab back to the Browser and rename it in
the same way you would rename any old clip. (This way, you have a copy
of the clip to apply elsewhere in the project.) Later, you can drag this
text as many times as you like into the Timeline. This approach is
handy when you need to reuse the same title more than once.


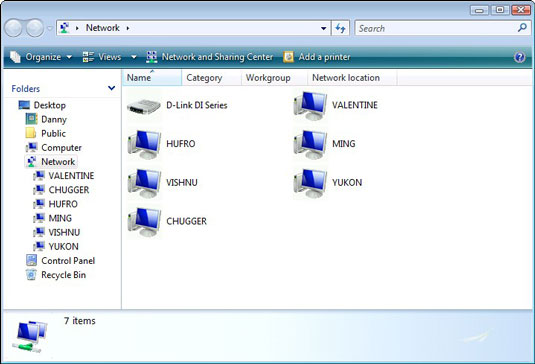 In Windows Vista, open a computer icon in the Network window, shown
above, to see whether any folders or disk drives are available.
In Windows Vista, open a computer icon in the Network window, shown
above, to see whether any folders or disk drives are available.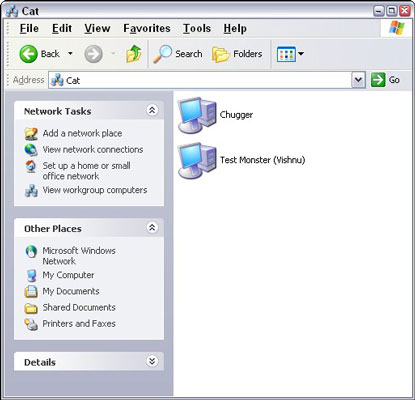 In Windows XP, shared
In Windows XP, shared 











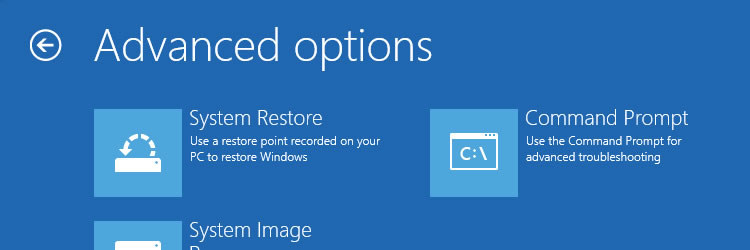 Windows 8
Windows 8
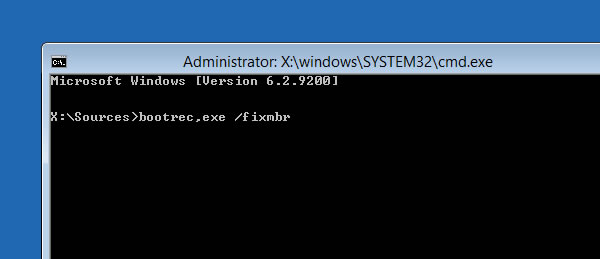
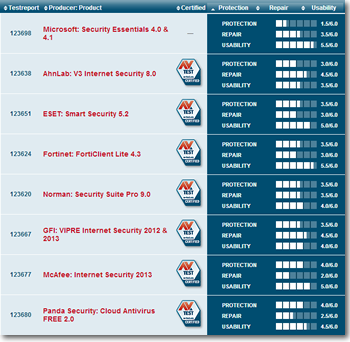
 Nvidia has
Nvidia has 













